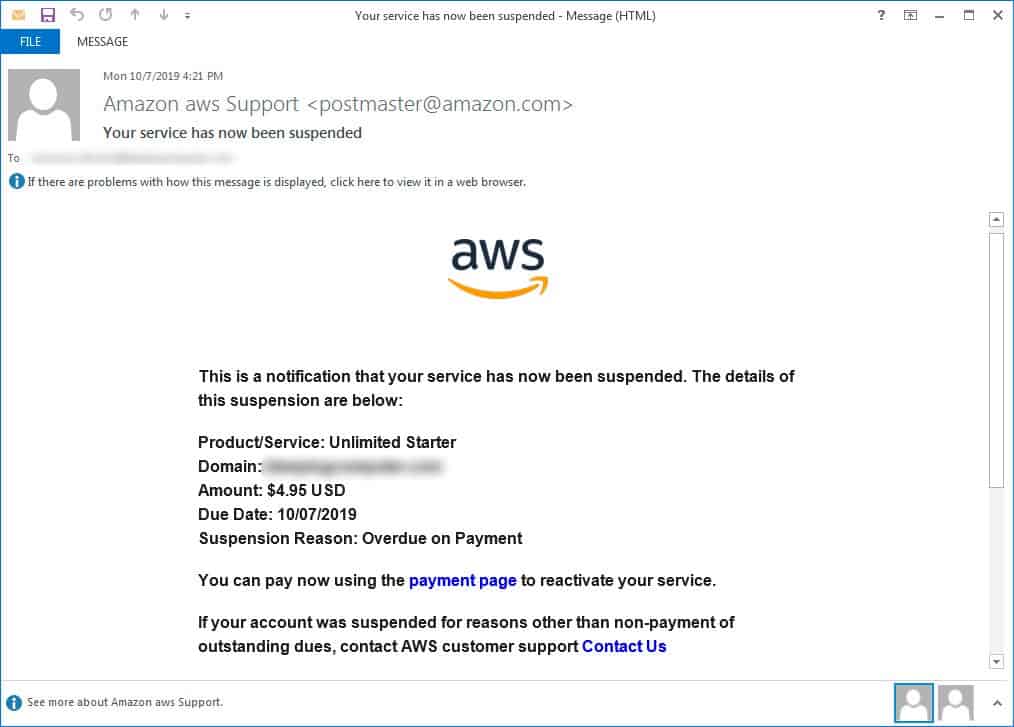
What makes this phishing mail different?
How to stay safe from this attack?
The attacker is able to do this by exploiting different open relay vulnerabilities that are yet to be patched. Hence, whenever you receive any such email, thoroughly check the authenticity of the mail. By checking the email sender address and the embedded URL. Think at least more than twice before entering your login credentials.